Understanding Linux Networking Commands: 5 Most Used Linux Networking Commands
In this article, we describe the most common uses of the top 5 Linux Networking Commands, providing examples and use cases.
TUTORIAL
Understanding Linux Networking Commands: 5 Most Used Linux Networking Commands
If you are using or administrating a Linux system, you are bound to work with its networking aspects: solving connection issues, supervising data exchange and flow, or simply setting up a device.
Knowing the basic network commands can greatly enhance your productivity as a Linux-based system operator. In this article, we describe the most common uses of the top 5 Linux Networking Commands with examples and use cases.
1. ip Command
The IP command is most useful for configuring and managing network interfaces or obtaining details about a specific IP. It succeeded in the traditional ifconfig application and provides greater capabilities and control.
Use Case:
To quickly identify the IP address of your server or workstation.
To manage network interfaces, such as enabling or disabling them:
Why do I need to disable the network interface?
Administrative Work: Eliminate the connection of certain network interfaces for troubleshooting or hardware maintenance.
Security: Restrict the interface such as changing configuration settings to disallow users or other components from making connections to the internal network or to outside networks.
Network troubleshooting: Remove out a specific interface to help narrow the source of network problems.
2. ping Command
The ping command uses ICMP echo requests to test the reachability of a remote host. Usually, it is the first tool utilized in a troubleshooting network.
Ping command can be used for IP addresses or domain names. In this example it sends 5 echo packets to google.com and reports back response times.
Use Case:
To test if a remote host is reachable.
To measure network latency in milliseconds (ms)
3. traceroute Command
The traceroute command provides a visualization of the path that packets follow from your system to a specified destination, detailing each intermediary hop encountered.
Example:
This command traces the route that packets take to reach Google's public DNS server.
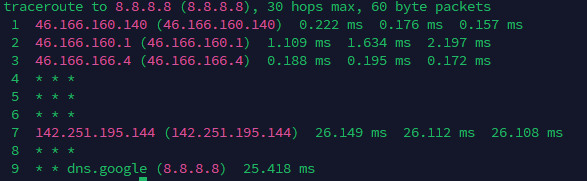
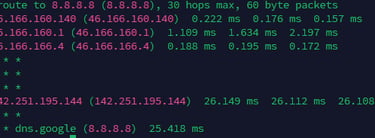
Explanation:
Destination: Traces the path to 8.8.8.8, Google's public DNS, with a maximum of 30 hops.
Hop 1: First router (46.166.160.140) responds with very low latency (~0.2 ms).
Hop 2: Second router (46.166.160.1) shows slightly higher latency (~1–2 ms).
Hop 3: Third router (46.166.166.4) also responds with very low latency (~0.2 ms).
Hops 4–6: No response (* * *), likely due to security settings or non-responding intermediate nodes.
Hop 7: Google’s network router (142.251.195.144) responds with ~26 ms latency.
Hop 8: Unresponsive hop (* * *), common in corporate networks.
Hop 9: Final destination (8.8.8.8) reached with ~25 ms latency.
Use Case:
To identify network bottlenecks or misconfigurations along the route to a host.
4. ss Command
Ss - Socket Statistics is offering valuable information regarding open sockets, listening ports, and active connections. It serves as a quicker and more sophisticated alternative to netstat.
Example:
This displays all TCP and UDP listening ports with numerical addresses.
Columns Explanation:
Netid: Protocol type (tcp or udp).
State: The socket's state (e.g., LISTEN for active listeners, UNCONN for unconnected).
Recv-Q / Send-Q: Receive and send queue sizes (0 means no data waiting).
Local Address:Port: The local IP and port where the service is listening.
Peer Address:Port: The remote address and port (often * for unspecified).
UDP Entries:
127.0.0.54:53 and 127.0.0.53%lo:53: DNS services running locally on port 53 for name resolution.
TCP Entries:
127.0.0.53%lo:53 and 127.0.0.54:53: DNS resolution via TCP on port 53 locally.
:22: SSH service is listening on port 22 and accepts connections from any IP ().
DNS: Both tcp and udp entries on port 53 are for local DNS queries.
SSH: The *:22 entry indicates an active SSH service allowing remote connections.

Use Case:
To identify which applications are using specific ports.
To troubleshoot issues with open or blocked ports.
5. dig Command
The dig (Domain Information Groper) command serves as a robust and versatile tool for querying DNS, essential for diagnosing and validating DNS configurations. It is capable of retrieving a wide array of DNS records, including A, MX, NS, TXT, among others.
Example:
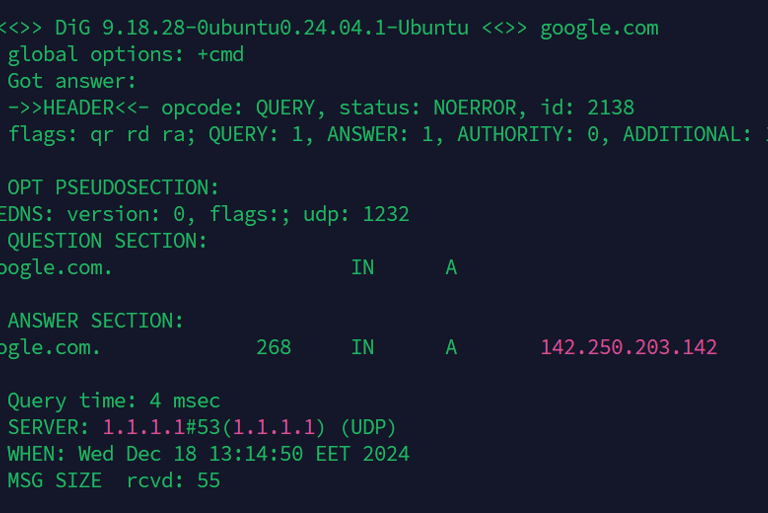
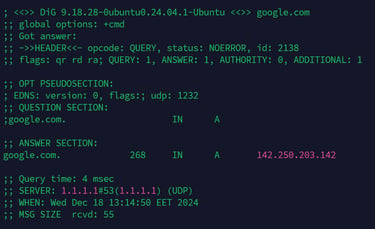
Explanation:
QUESTION SECTION: Shows the query submitted (google.com).
ANSWER SECTION: Presents the resolved IPv4 address (93.184.216.34).
QUERY TIME: The duration required to resolve the query (4 milliseconds).
SERVER: Specifies the DNS server utilized for the query.
Advanced Usage of dig command
dig example.com MX
This retrieves the mail exchange servers for example.com, useful for verifying email configurations.
dig example.com NS
This displays the authoritative name servers responsible for managing DNS records of the domain.
dig example.com TXT
Useful for retrieving domain verification records or SPF/DKIM configurations for email security.
dig -x 93.184.216.34
This performs a reverse lookup, resolving the IP address 93.184.216.34 back to its domain name.
You may also like: